 Developments in automotive industry cyber attacks.
Developments in automotive industry cyber attacks.
Of the many types of cyber attacks that exist globally, 2021 is perhaps the year that ransomware stepped into the forefront of everyone’s mind, according to Bob Maley, Chief Security Officer at Black Kite.
The Boston-based company, which caters to a global audience, has statistics that show that ransomware—a type of malware that can render a company’s systems inaccessible to varying degrees or steal data until a ransom is paid—is gaining serious ground.
“The bad actor community has figured out it is a tactic that plays very well. It’s very easy to identify targets,” said Maley in an interview with Canadian auto dealer. “Once they do that, it’s very easy to exfiltrate information to ask for demands of money to allow the systems to be recovered and a number of other things.”
Ransomware has been around for about two decades and has been growing over the past five or six years, according to Maley, but he said the uptick this year is significant. That should be a red flag for the broader retail industry (including automotive), as companies in this sector typically do not focus on online cyber security “hygiene.”
“The last year and a half was a bad year for retail, with the pandemic locking everybody down, and now they’re just starting to come back,” said Maley. “So they are struggling with having the staff, the money, and the income to really address these issues, which kind of makes them a target for the bad actors.”
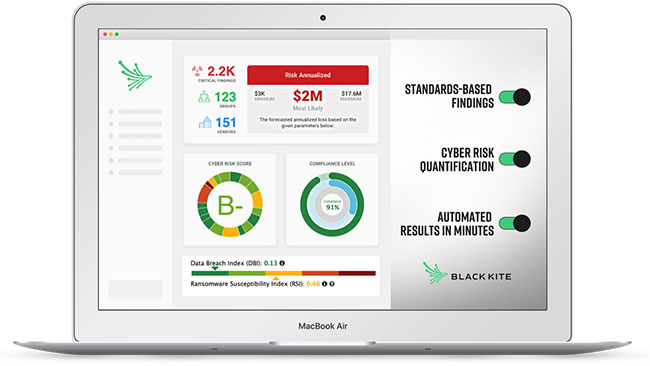
IMAGE credit: black Kite
How “bad actors” take advantage of your employees
One of the ways in which cyber hackers can take advantage of dealership employees through ransomware attacks is by getting them to divulge information. And one of the most common ways to do this comes when an employee uses their work credentials to log into systems outside of the office or work environment.
Google also has a software called Google authenticator that allows an out-of-band form of ensuring that the person is who they say they are.
Think Pinterest and similar social media sites, and imagine one of these sites being hacked and the company’s credential database appearing on the dark web—which actually happens on a regular, perhaps even daily basis, according to Maley. Hackers will take that information and use the credentials to launch cyber threats and/or attacks. And they have quite the incentive to do so.
An Upstream report on Global Automotive Cybersecurity for 2021 states that cyber crime “is more profitable than the global illegal drug trade,” and “is estimated at $600 billion a year.” It is also worth noting that a large number of these cyber crimes stem from the dark web.
Black Kite’s own report on Ransomware Risk for Automotive Manufacturing in 2021 shows that the digital transformation, which was accelerated by the pandemic, creates a larger attack surface. It states that the five most impactful ransomware issues for auto companies are:
- That there is at least one possible high-severity vulnerability due to out-of-date systems; 91 per cent of companies have more than 1,000 leaked credentials on the deep web, paving the way for phishing campaigns.
- That 90 per cent of these companies are susceptible to phishing attacks.
- Eighty-four per cent of the auto companies included in the study have publicly visible critical ports.
- At least one leaked credential was found on lists shared on the deep web in the last 90 days for 64 per cent of the companies.
- And 19 per cent experienced a data breach in the past.
“You look at auto dealerships, for instance, and some of the larger auto dealers have over a hundred different dealerships in multiple states, and they have to be connected somehow,” said Maley.
And they are. Nowadays, consumers can do a quick search of vehicle inventory across all of the company’s dealerships, online.
“To make that happen, you have to have communication between systems—and it’s that communication between systems that most of the time is not done in a very secure way,” said Maley.
A good example is the May 7, 2021 Colonial Pipeline ransomware attack. The company exposed some of their systems on the internet to make it easier to do work remotely via remote access ports. As The New York Times put it in a May 14 news analysis: “The hack underscored how vulnerable [the] government and industry are to even basic assaults on computer networks.”
Colonial Pipeline is an American oil pipeline system based in the United States that controls a significant portion (nearly half) of the gasoline, jet and diesel fuel moving along the East Coast, according to the NYT. The company paid nearly $5 million in digital currency to recover its stolen data, while consumers waited in long lineups as a reaction to the news, panic-buying gasoline.
The ripple effects of these attacks can be wide-ranging.
A few solutions, among many
So what can dealers do?
Maley advises ensuring dealership employees are educated about the basics: the use of their login credentials, not reusing passwords to get into the billing system, not using the same email and password to login to their social media account, and then for the dealership to also require the use of a multi-factor authentication for access to all of their important systems.
Google also has a software called Google authenticator that allows an out-of-band form of ensuring that the person is who they say they are.
“That’s actually something they can get for free. They just have to implement it in their systems,” said Maley, adding that there are “dozens of ways to multi-factor, but that’s just one of the simplest.”
Black Kite also offers a free service, where they developed a technology called the Ransomware Susceptibility Index that allows the company to understand what a “bad actor” is looking for to get into your systems. It shows how probable a particular company is in becoming the victim of a ransomware attack.
Black Kite also provides all the details of what makes the company in question susceptible to these attacks, and how to fix these issues. After that, it is up to the company to be observant, and to pay attention to those things moving forward.
Cyber threats and attacks are not new, but they are evolving. Hackers are constantly looking at new ways to trick your employees so they can access your systems.
“The funny thing about computer systems is that, if you put something out there today, in a couple of weeks, someone is going to install something they should not on a work system, and something will change as a result of that action,” said Maley.
Being prepared and understanding your dealership’s vulnerabilities can go a long way in saving you time, money, and a whole lot of headache.
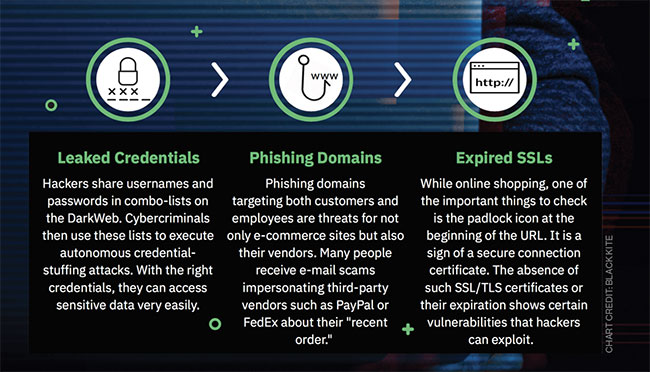
CHART credit: black Kite











